Imagine for a moment your company's most valuable secrets, the very things that make your business special, suddenly exposed or damaged. This frightening scenario is often not caused by an outside hacker, but by someone already inside, someone you might even trust. That, in a way, is the heart of an insider threat, and it's a topic that truly deserves our attention today, as of June 10, 2024.
Understanding what an insider threat means is, you know, pretty important for anyone involved with keeping an organization safe. It's not just about firewalls and antivirus software anymore; it's also about the people who have legitimate access to your systems and sensitive information. These individuals, whether they mean to or not, could cause serious harm.
This article will help you get a good grasp on what an insider threat is all about, why it matters, and how to spot the signs. We'll look at different kinds of these threats, talk about how they can hurt a business, and share some practical ways to keep your organization secure. So, stick around to learn how to keep your important stuff safe from within.
Table of Contents
What Exactly is an Insider Threat?
Why Insider Threats are a Big Deal
Different Kinds of Insider Threats
The Malicious Insider
The Negligent Insider
The Compromised Insider
Signs of a Possible Insider Threat
How to Protect Against Insider Threats
Strong Access Rules
Regular Training and Awareness
Monitoring Activity
A Good Culture
Common Questions About Insider Threats
Keeping Your Organization Secure
What Exactly is an Insider Threat?
An insider threat, basically, happens when someone who has authorized access to an organization's resources, like data, systems, or facilities, uses that access to harm the organization. This harm could be losing information, damaging systems, or even causing financial trouble. It's really about trust being broken, or sometimes, just a simple mistake.
The "insider" part is, you know, key here. It means the person is already trusted to some degree. They might be an employee, a former employee, a contractor, or even a business partner. Someone, in a way, who has a key to the building or a password to a system.
This is different from, say, a hacker trying to break in from the outside. An insider already has a foot in the door, or perhaps, is already sitting at a desk. This makes detecting and stopping them a bit more complicated, as a matter of fact.
The harm they cause can be, you know, pretty varied. It might be stealing customer lists, taking secret product designs, or messing up important company records. Sometimes, it's just deleting files out of spite.
Think of it this way: if your home has a good lock on the front door, that helps keep outsiders out. But if someone living in your house, or a trusted guest, causes trouble, that's a different kind of problem entirely. An insider threat is, in a way, very much like that.
Organizations, like the ones Business Insider has covered, often deal with this. They're very strict about ethical and safety issues, and they have no tolerance for harassment of employees or trading on insider information, which can be a form of insider threat itself. So, it's a big deal.
Why Insider Threats are a Big Deal
Insider threats are, you know, a very serious concern for many reasons. First, they can be incredibly hard to spot. Since the person already has legitimate access, their actions might look normal at first glance. It's not always an obvious breach, you know.
Second, the damage can be, you know, really extensive. An insider often knows where the most valuable data is kept, or which systems are most critical. They can go straight for the jugular, so to speak. This means the impact can be much worse than an external attack, sometimes.
Third, there's the trust factor. When an insider causes harm, it can really hurt morale within the company. Employees might feel less secure or less trusting of their colleagues. It's, like, a fundamental breach of the workplace community.
Financially, the costs can be, you know, enormous. There are direct costs from data loss or system repairs, but also indirect costs like damage to the company's reputation, legal fees, and regulatory fines. Business Insider, for instance, has covered how companies deal with these sorts of issues, highlighting the serious financial and reputational fallout.
And, you know, it's not just about money. Losing sensitive data can put customers at risk, or give competitors a huge advantage. It can even, you know, impact national security if the organization deals with critical infrastructure.
The original pitch deck that Business Insider covered, for example, might have contained valuable insights. If an insider had leaked that, it could have been a huge problem. It shows how important it is to protect all kinds of information, you know.
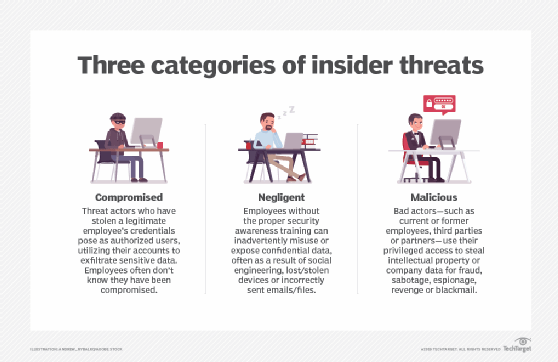
Different Kinds of Insider Threats
When we talk about insider threats, it's not just one type of person or one kind of bad act. There are, you know, several ways an insider can pose a risk. Understanding these different categories helps organizations prepare better.
The Malicious Insider
This is, you know, perhaps the type most people think of first. A malicious insider is someone who intentionally tries to harm the organization. They have a clear purpose, whether it's for personal gain, revenge, or even to support an outside group. They might steal data to sell it, destroy systems out of anger, or sabotage operations.
Their actions are, you know, deliberate and often well-planned. They might use their authorized access to gradually gather information or plant malware. This kind of threat is, basically, a betrayal of trust.
For instance, an employee who is leaving the company might decide to take customer lists with them to their new job. Or, someone who feels wronged by the company might delete important files on their last day. These are, you know, very direct acts of harm.
Business Insider, for example, has talked about companies that are very strict about ethical issues. This kind of insider, you know, directly violates those ethics.
The Negligent Insider
This type of insider threat is, you know, often unintentional. A negligent insider causes harm not because they want to, but because of carelessness, a lack of awareness, or simply making a mistake. They might click on a phishing link, lose a company laptop, or accidentally send sensitive information to the wrong person.
Their intentions are, you know, good, or at least not bad. They aren't trying to hurt the company. But their actions, or lack of proper care, still create a vulnerability. This is, basically, a very common form of insider threat.
For example, an employee might save a confidential document to a personal cloud storage service that isn't secure. Or, they might use a weak password that's easy for an external attacker to guess. These things happen, you know, quite often.
Training is, you know, very important for this group. Teaching people about security best practices can significantly reduce this kind of risk. It's about helping them understand the dangers, you know.
The Compromised Insider
A compromised insider is someone whose legitimate access is used by an outside party without their knowledge. This usually happens when an employee's account is hacked, or their device is infected with malware. The insider themselves is, you know, a victim, but their compromised credentials become a tool for an external attacker.
The external attacker then uses the insider's access to move around inside the network, steal data, or cause disruption. The insider might not even know their account is being used. It's, like, a Trojan horse scenario.
This could happen if an employee falls for a sophisticated phishing email that steals their login details. Or, if their personal computer, which they use for work, gets infected with a virus that then spreads to the company network. These situations are, you know, pretty tricky.
The complex that was attacked by Islamic State militants in 2017, for instance, shows how external forces can exploit vulnerabilities. While not strictly an insider, it highlights the danger of a compromised entry point, you know. Protecting against this involves strong cybersecurity measures for all users.
Signs of a Possible Insider Threat
Spotting an insider threat isn't always easy, but there are often behavioral or digital clues. Knowing what to look for can, you know, really help. It's about noticing things that seem a little off.
One sign might be unusual access patterns. If an employee starts trying to access files or systems they don't normally need for their job, especially outside of working hours, that's, you know, a red flag. Or, if they suddenly try to access very sensitive information.
Another sign could be a change in behavior. Someone who is suddenly very secretive, or who expresses strong dissatisfaction with the company, might be worth watching. This isn't about judging people, but about recognizing potential risk factors, you know.
Copying large amounts of data to personal devices or cloud storage is, you know, also a big warning sign. If someone is suddenly downloading gigabytes of information, especially if their job doesn't require it, that's a problem.
Attempts to disable security tools or bypass security protocols are, you know, also very suspicious. If someone is trying to turn off antivirus software or get around firewalls, they probably have a reason, and it's rarely a good one.
Frequent complaints about workload or feeling undervalued could also, you know, be a precursor to malicious activity, though it's important to remember these are just potential indicators, not proof. It's about looking at the whole picture, you know.
Finally, observe if an employee is trying to recruit other employees to help them with unusual activities. This could be, you know, a sign of a coordinated effort.
How to Protect Against Insider Threats
Protecting against insider threats requires, you know, a multi-faceted approach. It's not just one thing you do; it's a combination of policies, technology, and a good workplace culture.
Strong Access Rules
One of the most effective ways to limit insider risk is to follow the principle of "least privilege." This means giving employees only the access they absolutely need to do their job, and nothing more. If someone doesn't need access to the financial records, they shouldn't have it, you know.
Regularly reviewing and updating these access permissions is, you know, also very important. When an employee changes roles, their access should be adjusted. When they leave the company, their access should be immediately revoked. This is, you know, a fundamental step.
Using strong authentication methods, like multi-factor authentication, also adds a layer of security. This makes it much harder for a compromised account to be exploited, you know.
Regular Training and Awareness
Many insider threats, as we talked about, are accidental. So, educating employees about security risks and best practices is, you know, very important. This includes training on phishing, secure password habits, and how to handle sensitive information.
Making security awareness a continuous process, not just a once-a-year lecture, is, you know, key. Reminders, quick tips, and real-world examples can help keep security top of mind. It's about building a culture where everyone feels responsible for safety, you know.
We are strict about ethical and safety issues, for instance, and this kind of training supports that. It helps people understand why certain rules are in place, you know.
Monitoring Activity
Monitoring employee activity on company systems can help detect unusual behavior. This isn't about spying, but about looking for patterns that might indicate a threat. This could involve tracking data downloads, login times, or access attempts to sensitive files.
Tools that can flag suspicious activities, like attempts to access systems outside of normal working hours or large data transfers, are, you know, very useful. These tools can alert security teams to investigate further.
It's important to do this transparently and ethically, of course. Employees should be aware that their activity on company systems is monitored. This helps maintain trust while still providing necessary security oversight, you know.
A Good Culture
Building a positive and supportive work environment can, you know, also reduce the likelihood of malicious insider threats. Employees who feel valued and respected are less likely to seek revenge or feel the need to steal.
Having clear channels for employees to voice concerns or grievances can help address issues before they escalate. It's about listening to people and creating a place where they feel heard, you know.
As "My text" states, organizations have no tolerance for harassment of employees. This kind of stance fosters a better environment, which in turn helps with security. A happy employee is, you know, less likely to become a problem.
Common Questions About Insider Threats
People often have questions when they first start learning about insider threats. Here are a few common ones, you know, that might help clarify things.
What are common examples of insider threats?
Common examples, you know, include an employee stealing customer data before leaving for a competitor, a disgruntled staff member deleting critical files out of spite, or someone accidentally sending a confidential report to the wrong email address. Another example is an employee falling for a phishing scam, which then allows an attacker to use their login to access company systems. These are, you know, very real situations.
How can an organization stop insider threats?
Stopping insider threats involves several steps, you know. Organizations can implement strict access controls, so people only see what they need. They can also provide regular security training to help employees recognize risks. Monitoring system activity for unusual patterns and fostering a positive work culture where employees feel valued are, you know, also very important strategies.
What is the difference between a malicious and a negligent insider?
The main difference is, you know, intent. A malicious insider acts with a clear purpose to harm the organization, like stealing data on purpose. A negligent insider, on the other hand, causes harm unintentionally, often due to a mistake or carelessness, like accidentally losing a company laptop. Both can cause damage, but their motivations are, you know, very different.
Keeping Your Organization Secure
Understanding what an insider threat is, and how it can affect an organization, is, you know, a very important first step in protecting against it. It's a continuous effort that involves both technology and, you know, a lot of focus on people.
By putting in place strong policies, educating employees, and keeping an eye on system activity, businesses can significantly reduce their risk. Remember, the goal is to create a secure environment where trust is maintained, and potential issues are caught early. To learn more about cybersecurity best practices on our site, you can explore further.
It's about being proactive and creating a culture where everyone plays a part in keeping information safe. This helps ensure that the valuable insights and data your company holds remain secure, allowing your business to thrive without unnecessary risks. You can also link to this page for more detailed information on specific security measures. For more general information about cybersecurity, you might find resources like the CISA website helpful.


Detail Author:
- Name : Erika Medhurst
- Username : wjones
- Email : lon.wolff@gmail.com
- Birthdate : 1986-08-07
- Address : 10168 Rogahn Mill West Douglas, RI 12208
- Phone : 320.956.5027
- Company : Stiedemann, Nitzsche and Hoppe
- Job : Fiberglass Laminator and Fabricator
- Bio : Similique assumenda molestiae ullam omnis. Cum nihil et omnis consequatur sed. Rerum nulla dolor qui nostrum suscipit repellendus. Nam nobis fugiat ut non nemo.
Socials
tiktok:
- url : https://tiktok.com/@aoberbrunner
- username : aoberbrunner
- bio : Natus et illum veniam quisquam qui veniam ducimus.
- followers : 1819
- following : 1823
instagram:
- url : https://instagram.com/araceli4579
- username : araceli4579
- bio : Id qui ea expedita. Illo praesentium occaecati consectetur quis maxime in.
- followers : 344
- following : 2012
linkedin:
- url : https://linkedin.com/in/araceli_official
- username : araceli_official
- bio : Eligendi necessitatibus dolorem corporis.
- followers : 464
- following : 2272